Covert spy operation hacks Syrian military phones via former first lady’s fake charity app details
A covert surveillance operation reportedly compromised the smartphones of thousands of Syrian military officers through a fake mobile app posing as a charitable initiative backed by Syria’s former First Lady, Asma al-Assad.
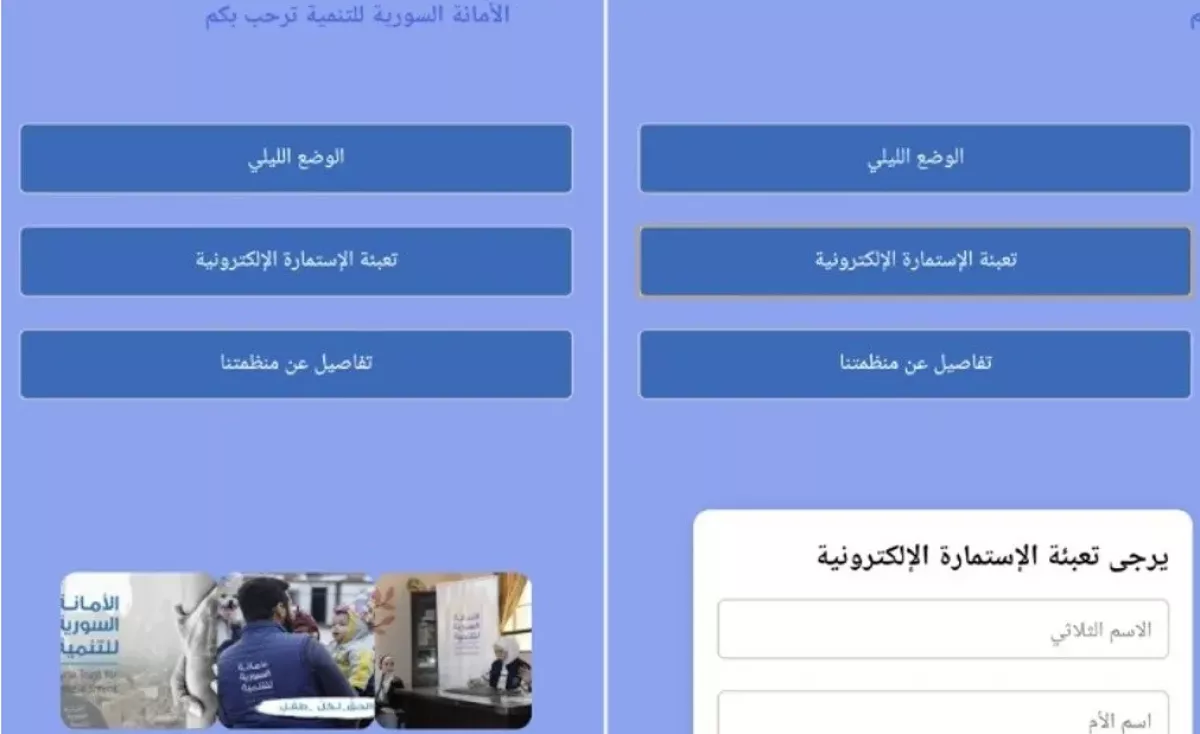
The app—named Syria Trust for Development —was distributed to Syrian officers through Telegram channels. Promising financial aid in the form of donations, the app encouraged users to enter personal information through an external website, Caliber.Az reports via Turkish media.
However, the site was part of a phishing scheme designed to collect sensitive data. The application was allegedly developed to impersonate a foundation linked to Asma al-Assad.
The use of her name reportedly helped the app gain quick trust and widespread adoption, particularly among officers in high-ranking and sensitive positions. It included form fields such as “What kind of assistance do you need?” and “Can you provide details of your financial situation?”—questions that seemed innocuous but were intended to extract detailed personal and professional information.
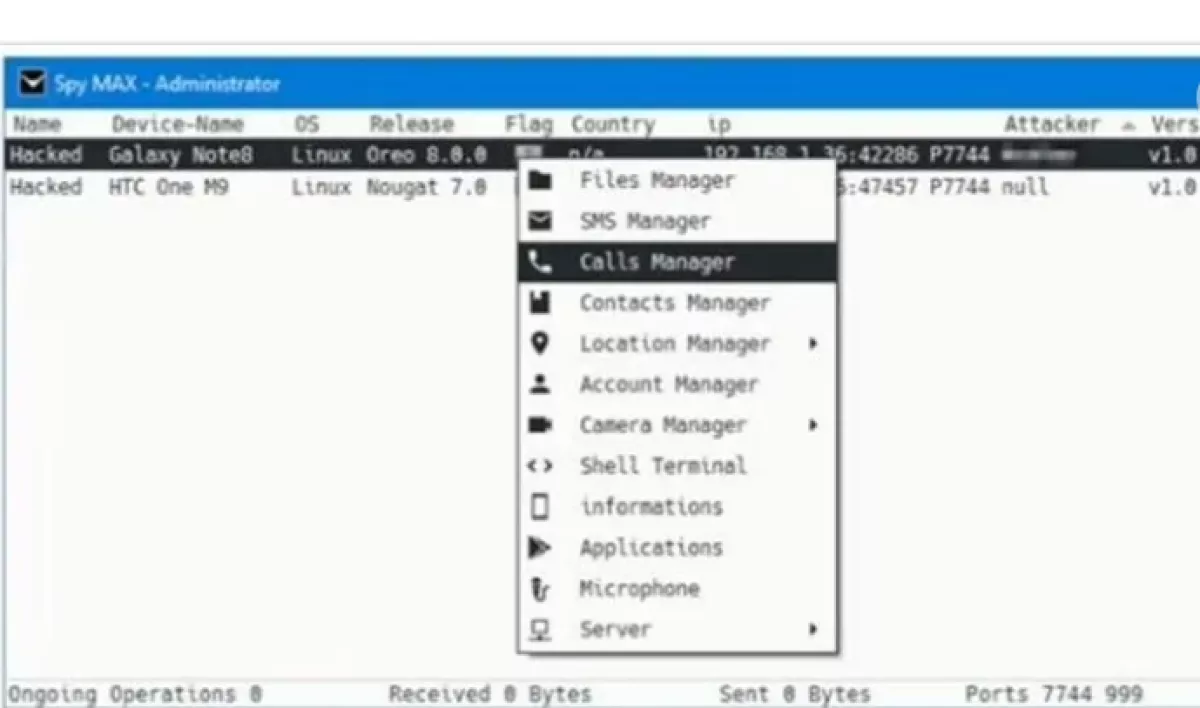
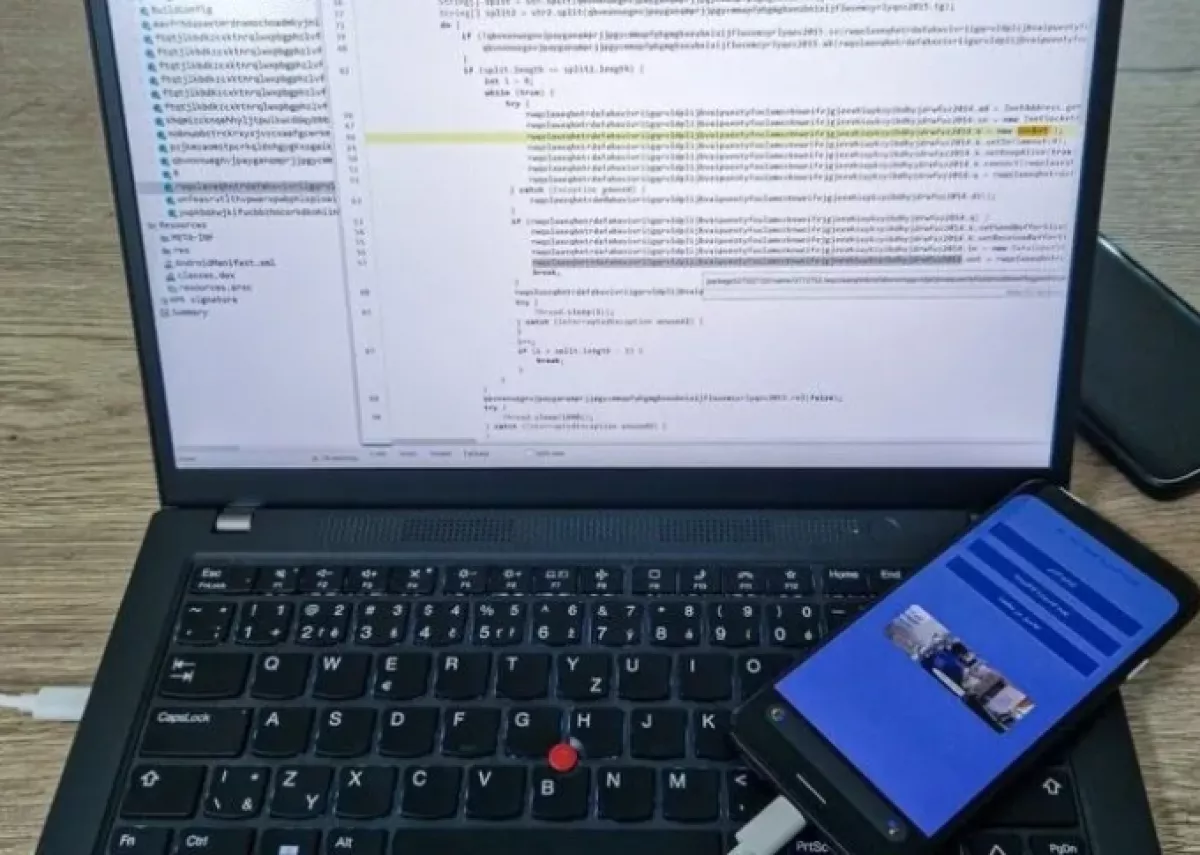
Unaware of the true nature of the app, many officers disclosed information about their identities, family members, and military roles. This enabled the creators to build a comprehensive intelligence map of the Syrian Armed Forces, particularly targeting commanders, communications officers, and intelligence personnel. The second phase of the operation reportedly involved the stealthy installation of SpyMax, a powerful Android-based spyware tool.
Delivered through malicious APK files, the malware granted full remote access to infected devices. According to the report, this included control over microphones, cameras, messaging apps, photo galleries, and even real-time GPS tracking.
By Naila Huseynova








